Read Owasp Secure Coding Practices Quick Reference Guide
Software threats have grown at an exponential charge per unit in the last few years. Vulnerabilities in software and applications have caused a lot of damage to different organizations and people. The image below categorizes the severity of vulnerabilities identified in applications:
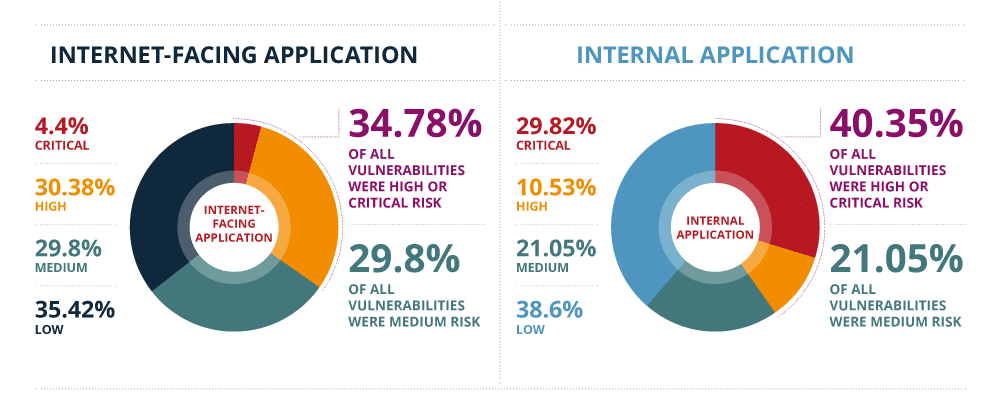
Source: EdgeScan 2020 Vulnerability Statistics Report
Secure coding standards and best practices enable developers to develop applications and software deeply. These standards ensure that software developers lawmaking their applications securely without leaving any vulnerabilities that may be exploited past different threat actors.
Although there are a number of ways to securely develop applications, OWASP(Open up Web Application Security Project) provides a comprehensive secure coding checklist. This secure coding checklist primarily focuses on web applications, simply it tin exist employed every bit a security protocol for every software development life cycle and software deployment platform to minimize threats associated with bad coding practices.
OWASP provides the following secure coding checklist which has a number of prevention techniques through which damage of different types of software attacks can be minimized and mitigated. We are going to list some of the techniques which come nether each of the check list.
Input Validation
Input validation or information validation is a proper check/examination administered on input supplied by users or the application. Below is a lawmaking snippet that validates input in HTML5 for web browsers:
Source : W3Schools
The input provided checks thoroughly for any parameters that cause the application or software to carry abnormally that can lead to attacks such as injection, buffer overflows and cantankerous site scripting. Some techniques that tin be used to perform input validation are:
- Conducting data validation on trusted systems.
- Conduction validation and identification of data in terms of trusted and untrusted sources.
- Validating data based on data type, range and length of input against a list of immune characters.
- Checking and validating that the values in headers of requests and responses are only in ASCII characters.
- Validating all data provided by the customer/user before the data is candy, including URLs, HTTP headers, embedded lawmaking etc.
Output Encoding
Output encoding involves translating user input/unsafe information in such a fashion that when the input is displayed information technology does not execute every bit a lawmaking in a browser or plan. Using this technique, untrusted data in a grade that the interpreter does not sympathize is prevented from beingness executed.
Cross-site scripting attacks can be avoided using output encoding. Below is an example of what happens in a cross site scripting attack when an aribitary code is added into the input fields and output encoding is not taken care of.
Some of the techniques pointed out by OWASP are:
- Validating data on a trusted organization.
- Encoding all characters unless they are deemed safe for the target interpreter.
- Sanitizing untrusted data output using OS commands.
Authentication & Password Management
A user's identity is recognized using the authentication process. Password management involves a gear up of rules and techniques that should be followed past users when storing passwords in order to retain confidentiality and availability to sure critical avails/resource. OWASP mentions different techniques for this:
- Require authentication for all resources/pages that link to CIA Triad.
- Prevent the re-using of passwords.
- Notify users when countersign reset occurs.
- Report the number of login failure to the user upon their side by side successful login.
- Keep a short expiry time for temporary passwords that needs to be changed upon side by side login.
- Require passwords to be assail the basis of password complexity policy.
Session Management
The process of deeply treatment multiple requests from a service of a web application from different users is known equally session direction .
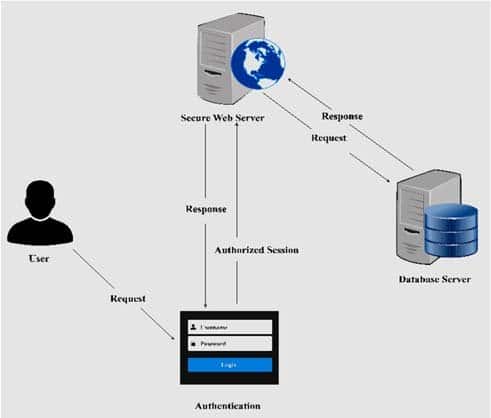
Source: Enquiry Gate
The following are some points on session management from the OWASP checklists:
- Sessions and connections should be fully terminated upon logout.
- Multiple logins should non exist allowed against the same User ID.
- Based on the risks and business objectives, session inactivity timeout interval should be as depression equally possible.
Access Control
Access control is a security technique in which users are given the right to access resources or systems on the basis of their privilege level. Out of a wide range, some techniques of access control are given below:
- Just authorized users should have admission to protected URLs, services, application information, user data, attributes etc.
- Account auditing should be implemented and unused accounts should be deleted.
- Accounts associated with different services to external or internal systems that are primarily used for non-critical tasks should be given to the lowest degree privilege.
- The number of transactions should be limited for a single user or device during a particular period of time.
Cryptographic Practices
Cryptographic operations are usually washed to encrypt sensitive data so that only intended users tin run across and brand changes to the data, thus maintaining confidentiality. Some of the cryptographic practices are mentioned below:
- A trusted system should exist used to implement cryptographic functions to maintain confidentiality of sensitive data on the awarding.
- The generation of random numbers, file names, GUIDs and strings should use an approved random number generator.
- Cryptographic cardinal management should exist employed by developing and using processes and policies.
- Master keys should exist protected from unauthorized access.
Error Handling & Logging
Fault handling involves procedures that handle unsolicited output, normally experienced when a plan or software is supplied with an abnormal input. Logging enables you to keep rails of the changes to a software or awarding. Fault handling and logging procedures/techniques are equally follows:
- Error handlers that practice not throw out debugging information in example of unsolicited input should exist used.
- When error weather condition occur, memory should be properly freed.
- Logs should non store sensitive data related to systems, sessions etc.
- Logs related to input validation failures, authentication attempts, access control, arrangement exceptions, unexpected changes to data and changes fabricated to security configurations should be maintained and checked thoroughly.
Data Protection
Data protection is the process involving safeguarding of important information from alteration, compromise or loss. The following techniques can be used to protect data in order to maintain confidentiality, integrity and availability:
- Follow the principle of least privilege by limiting user rights and privileges to those systems, information and usability that are required to accomplish the required goals and objectives.
- Exclude sensitive data from Get requests found in HTTP.
- Protect server-side code and preclude it from existence accessible past the common user. Proper access command should exist implemented for critical and sensitive data.
- Autocomplete feature should be excluded while inbound data into forms on websites or applications.
Advice Security
All sensitive information is protected past the apply of encryption. Send Layer Security (TLS) can be used for protecting connections in conjunction with different variants of encryption.
- In the case of TLS, failed connections should not downgrade to unsecure protocols.
- For protection of sensitive information over external sources utilize TLS.
- All connections should be specified with character encoding.
System Configuration
The following checklist should exist followed for organisation configurations:
- Ensure that systems, frameworks and system components are running latest versions and patches.
- Application of to the lowest degree privilege should exist on services accounts, webservers and processes.
- HTTP response headers should only include relevant information. Os, webserver version and software frameworks information should non exist included.
- Test and development environments should exist isolated from production environment.
Database Security
Database security involves security measures that assistance preclude diverse threats related to databases.
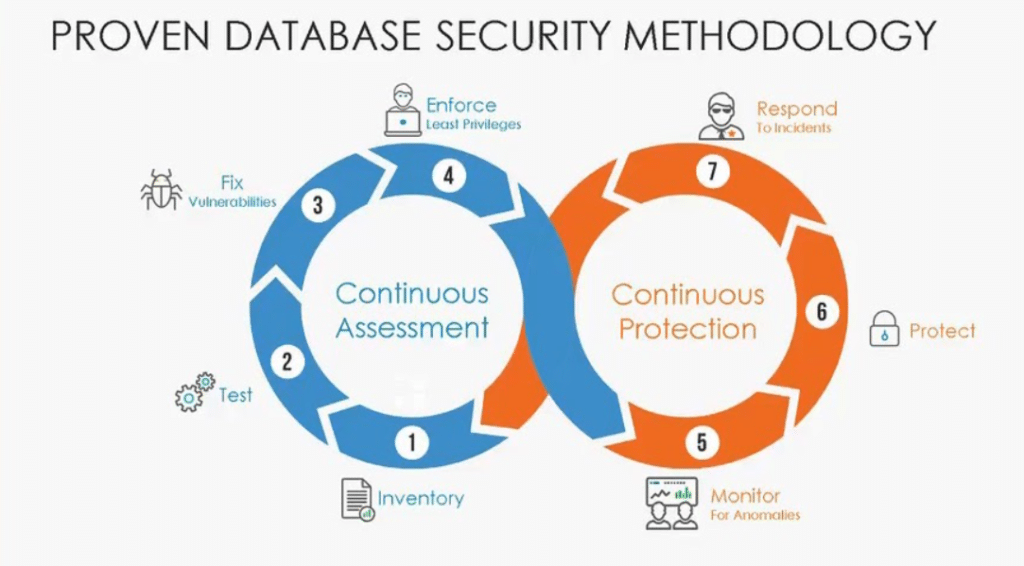
Source : Trustwave
Some of the techniques related to database security are as follows
- While accessing the database, the awarding should use lowest possible level of privilege.
- Default passwords should be inverse immediately. Password hygiene should be kept in mind while assigning passwords to accounts.
- Enable multifactor authentication where applicable. Disable default accounts that are not necessary for business requirements.
File Management
The following are some of the measures and techniques provided by OWASP:
- Ensure authentication while uploading a file on the server.
- Files uploaded on the server should exist validated by checking the file headers.
- Execution privileges should be turned off in the directories where files are uploaded.
- Absolute file path should never be sent to the customer.
Memory Management
Memory management is a very important aspect when dealing with applications and software as many attacks are related to memory. The following steps could be taken in gild to properly manage retention:
- Vulnerable functions such as impress, strcat, strcpy etc. should be avoided.
- Buffer size should exist checked for overflows.
- Input strings should be truncated properly before functions like copy and concatenation are used.
Determination
Incorporating the in a higher place-mentioned techniques in your software and spider web application earlier it is released in the production environs tin can surely relieve you lot from various attacks that somewhen compromises the CIA Triad.
Source: https://www.securecoding.com/blog/owasp-secure-coding-checklist/
0 Response to "Read Owasp Secure Coding Practices Quick Reference Guide"
Post a Comment